U2F Authenticatie
FEITIAN KEY TECHNICAL OVERVIEW
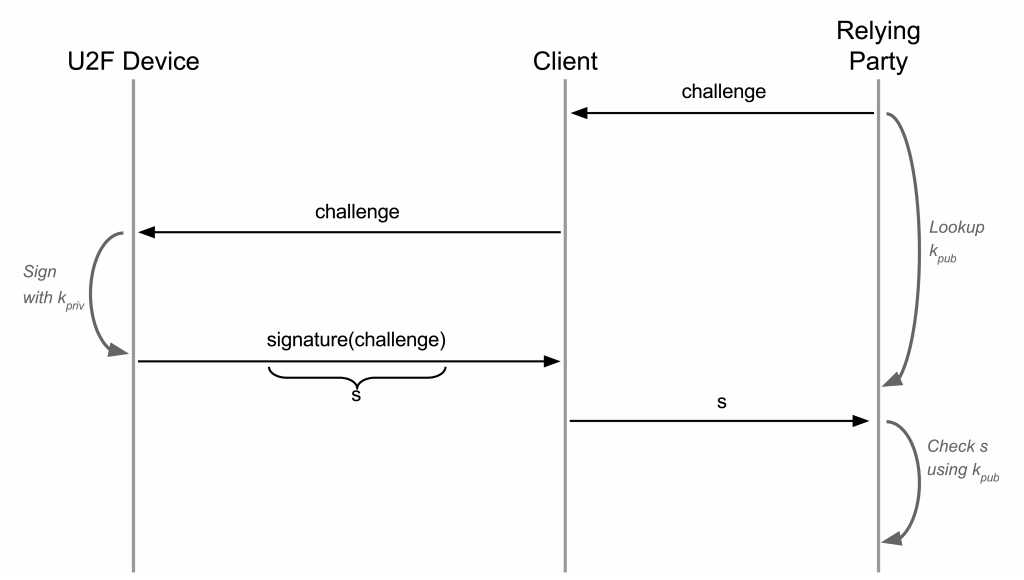
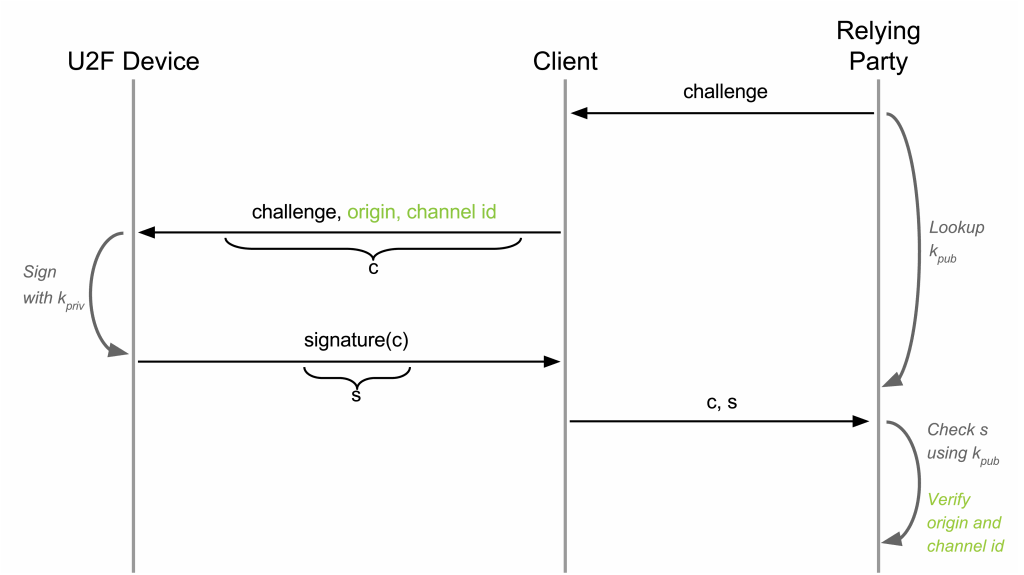
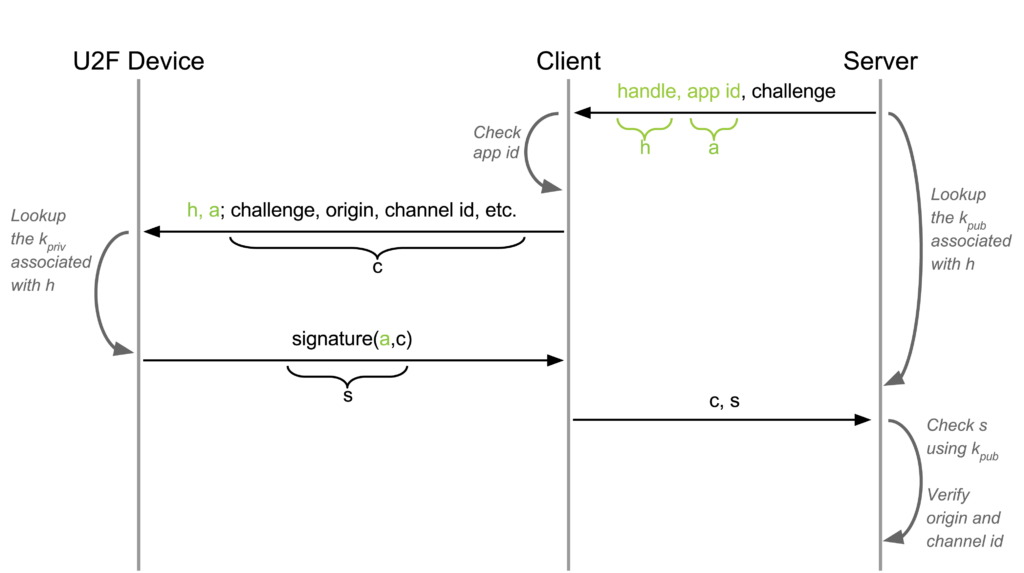
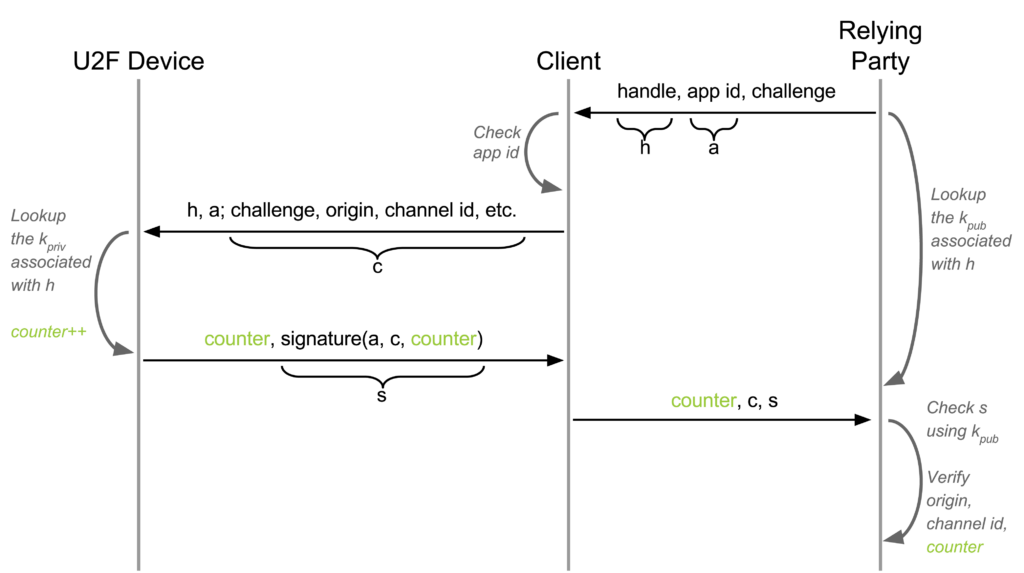
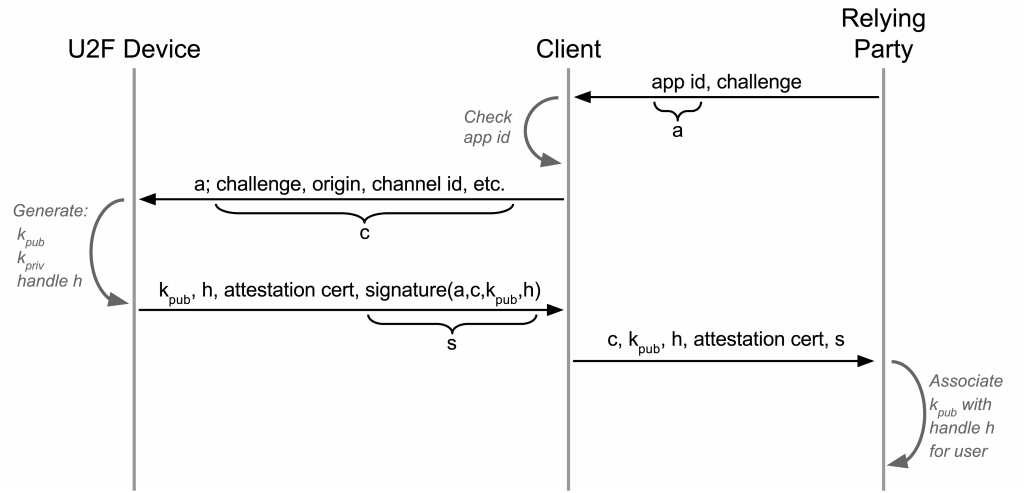
U2F is a challenge-response protocol enhanced with protection against phishing and Man-In-The-Middle attacks, application-specific keys, device cloning detection, and device attestation. There are two processes: registration and authentication.